iStat Pro is an Awesome Free System Monitoring Widget
June 26, 2009 Reading time: 4 minutes
Update: It's dead, Jim.
![]() For Mac OS 10.4 or higher: iStat pro is a system monitoring widget that has it all.
For Mac OS 10.4 or higher: iStat pro is a system monitoring widget that has it all.
iStat pro – Main site (update: link is now dead, unfortunately)
Like any system monitor worth its salt, iStat pro displays vital information about your:
- CPU
- Memory
- Hard disk(s)
- Network
- Temps
- Fan speed
- Battery (for laptops)
- Uptime and System load
- Running Processes Read more
TipsFor.us Giveaway – Win an iPod Touch 8 GB
June 25, 2009 Reading time: 4 minutes
Important: this contest is valid for USA residents only. Our apologies to our readers outside the US.
TipsFor.us is giving away a brand new iPod Touch! It’s beautiful.
This lovely gadget has 8 GB of storage – enough for roughly 1,750 songs, 10,000 photos, or 10 hours of video. It has a glorious 3.5-inch widescreen multi-touch display with 480-by-320-pixel resolution.
The iPod Touch is far more than just a music player. You can view photos, watch movies and YouTube, surf the web, check e-mail, play games, browse the App Store, and even read Amazon Kindle books.
Feeling adventurous? You can also install Skype/Fring on your new iPod Touch to make calls and send text messages.
Did we mention that it’s beautiful? Just look at it. Read more
WinCDEmu Integrates Disk Image Mounting in Windows Explorer
June 24, 2009 Reading time: 3 minutes
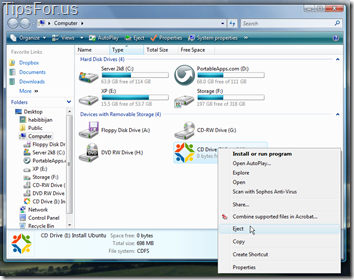 We’ve written before about Virtual CloneDrive, software that can mount and run disk images as if they are physical disks. A similar free program is WinCDEmu.
We’ve written before about Virtual CloneDrive, software that can mount and run disk images as if they are physical disks. A similar free program is WinCDEmu.
WinCDEmu – Main site
WinCDEmu – SourceForge page
WinCDEmu is free and open-source, and makes mounting a disk image (*.ISO, *.CUE, *.BIN, *.RAW, and *.IMG) as easy as double-clicking.
In case you are not familiar with disk images, here’s what you need to know: an image is the re-creation of the contents of a CD or DVD saved into a single file. That file will have an extension such as *.ISO, the most-common type.
These disk images are typically burned back onto a CD or DVD using disk-burning software such as InfraRecorder (free). For instance, if you want to download and use a Linux distro, you typically download the ISO and then burn it to a CD, thus allowing you to boot and run from that physical disk. Read more
Disable the “Install Updates and Shut Down” Option in Windows
June 22, 2009 Reading time: 3 minutes
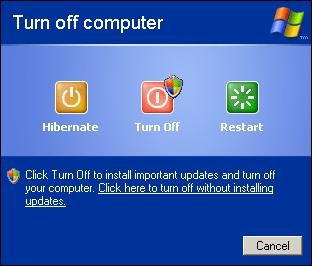 Have you ever been annoyed at the Install Updates and Shut Down message that displays after Windows Update runs in the background?
Have you ever been annoyed at the Install Updates and Shut Down message that displays after Windows Update runs in the background?
It’s easy to avoid this message entirely and force any pending updates to stay associated with the yellow shield in the system tray. This is one setting that I always configure for any machine under my control, mainly to inspect any pending updates before I choose to install them. It’s also handy for avoiding the dreaded WGA notification tool.
On to business: this tip works on XP, Vista, and Windows 7.
First, launch the Group Policy editor by going to Start – Run, and typing:
gpedit.msc
Note: if you don’t see the Start -> Run button, just press the Windows key + R. Read more
Do You Know What a Browser Is?
June 20, 2009 Reading time: ~1 minute
Well, this video explains why we have to bleed out our anus to make CSS sites and HTML emails work with IE and AOL.
Securing a Linux Server: SSH and Brute-Force Attacks
June 15, 2009 Reading time: 12 minutes
If you have a web server, then you are the target of many possible attacks. *ANY* port you have open on that server can be exploited, so you if you value your uptime and your data, you need to secure it. This article focuses on locking down your SSH configuration and user permissions.
If you’ve had your server online for a while without locking down your SSH configuration, have a look at this file: /var/log/secure and see if you’ve got a lot of connection attempts.
This is what a brute-force attack looks like:
[prompt]$ sudo less /var/log/secure
May 31 22:42:12 yourdomain sshd[25711]: Failed password for invalid user alberto from 190.2.35.25
port 32976 ssh2
May 31 22:42:12 yourdomain sshd[25712]: Connection closed by 190.2.35.25
May 31 22:46:11 yourdomain sshd[25714]: Connection closed by 190.2.35.25
May 31 22:56:46 yourdomain sshd[25717]: Invalid user neil from 190.2.35.25
May 31 22:57:10 yourdomain sshd[25717]: reverse mapping checking getaddrinfo for customer-static.someisp.com failed - POSSIBLE BREAK-IN ATTEMPT!
Using Geobytes (or a similar IP address locator), I can see that some hacker-bot in Argentina was guessing both usernames (e.g. alberto, neil) and passwords every few seconds. F*#K!! Read more