Top 5 Script Kiddie Mistakes
July 10, 2013 Reading time: 5 minutes
These are the most common and most annoying mistakes I see in web development code on a daily basis. Well, Ok, it’s the things that annoyed me most TODAY, but it’s not unique. It’s mostly PHP and MySQL stuff here, but the same abuses take place anywhere the language allows it.
1. Database prefixes. I find so many database tables that use a “table” or a “tbl” prefix. Are you serious? Do you think we don’t already know it’s a table we’re looking at? Likewise, some developers find it somehow necessary to use “column” or “col” in their column names. I mean really… do you pin your own name upside down on your shirt? Seriously, this type of labeling is completely unnecessary and it probably reveals you as the half-baked amateur that you are. Label your column names descriptively: too little info is bad, but too much is no better.
The one exception I make to this rule is this: be verbose with your primary keys because you’ll use those in all of your join statements. I know it’s easier to code if every table uses the ubiquitous “id” as the primary key, but if you ever have to do complex MySQL joins for reporting queries you’ll appreciate the fact that user_id or post_id references the same thing no matter which table it’s used in. Read more
Securing Your Email via 2-Step Verification
January 11, 2013 Reading time: 3 minutes
It is vitally important to keep your email account as secure as possible. Google is one organization that emphasizes security, so take advantage of it! For Google Mail, it is easy to enable 2-step authentication. The idea is simple: in order to log in, you must provide something that you know (your password) and something that you have (your phone).
Think about this for a moment… normally if someone gets ahold of your email password, they could read your email (or impersonate you!). Think about it a bit more: once a hacker is in your email, they can visit other sites (like Facebook, PayPal, or ???) and they can easily click the “I Forgot my Password” link, and POOF: they’ll be able to log into any site that uses that email address.
The bottom line is that a hacked email account can start a chain reaction that can destroy your digital life. But with Google Mail, there are steps you can take to prevent this. Read more
Review of Web-based Project Management Software
December 30, 2011 Reading time: 10 minutes
Help! I gotta keep track of everything I gotta do! There is help available to track your projects, you just got to know where to look.
A lot of developers, designers, students, and even web-hobbyists have a lot of items on their to-do lists for any particular site or project. You have to remember to fix that one CSS glitch, or rewrite a page to use some new function… the lists can be long and daunting. If you’re like me, you’re likely to forget half the stuff you need to do, and if it weren’t for project management software, I might as well stay in bed.
To put it mildly, there are *a lot* of applications out there that help you track bugs and manage projects, and this article only looks as a handful of them. Although the general purpose of these web-applications are similar, there are substantial differences in the pricing models, features, and usability, and hopefully this article will help you identify an application that is right for you. Or, if you’ve never really thought about using one before, maybe this article can help show you why project management / bug tracking software is good to have around. Read more
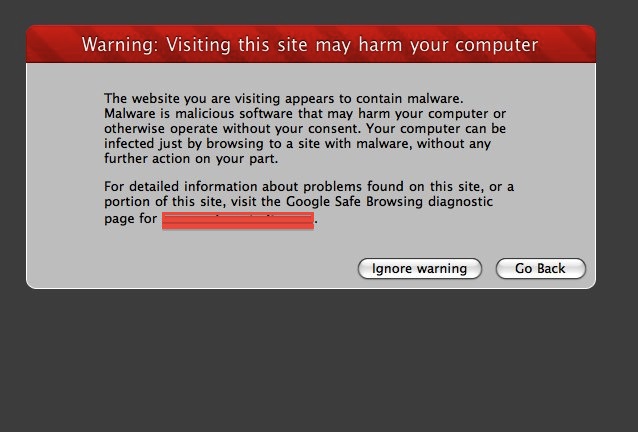
Basic Web Security
May 10, 2010 Reading time: 13 minutes
Web security is a huge topic, and this article only intends to cover some of the most basic issues and increase awareness of how carelessness or ignorance can lead to exploits. Ultimately, what you don’t know can hurt you, so it’s in your best interest to learn as much as you can about your site and the technologies it relies on. Here’s a brief run-down of some fairly common mistakes I’ve come across and what you can do to either avoid them or lessen your vulnerability.
Networx – Free Bandwidth Monitoring Software (Getting the Most Out of It)
August 1, 2009 Reading time: 13 minutes
Systems: Windows Only (2000, XP, Vista, 2008 / Both 32 and 64 bit)
Donationware: Technically it’s free, but when you see the level of craftsmanship in this program, you will want to donate.
Website: Softperfect.com
 I recently changed ISPs to one with much more consistent service, but the trade off is that I now have a rather small bandwidth cap. As much as we hate them, bandwidth caps are probably in all of our futures. The important thing is to have control over and be informed of your usage (before the bill arrives). I needed a reliable way to keep track of my bandwidth, so I tested out several free bandwidth monitoring softwares. My ISP has its own online bandwidth usage calculated, but I wanted a redundant system (one which I could use to make sure they were honest in their tracking). In my experiments, I found Networx to be the best. Its primary virtue is its ability to be as advanced as you need it to be. For my multiple computer home network, it has every feature I could ask for. Let’s take a closer look.
I recently changed ISPs to one with much more consistent service, but the trade off is that I now have a rather small bandwidth cap. As much as we hate them, bandwidth caps are probably in all of our futures. The important thing is to have control over and be informed of your usage (before the bill arrives). I needed a reliable way to keep track of my bandwidth, so I tested out several free bandwidth monitoring softwares. My ISP has its own online bandwidth usage calculated, but I wanted a redundant system (one which I could use to make sure they were honest in their tracking). In my experiments, I found Networx to be the best. Its primary virtue is its ability to be as advanced as you need it to be. For my multiple computer home network, it has every feature I could ask for. Let’s take a closer look.
The software is so unobtrusive; it even lacks a full control window. Instead, you can access all aspects of the software from the taskbar icon. Read more
Weekend Fun – Drive Yourself Crazy Playing Red Square
April 17, 2009 Reading time: 3 minutes
Looking to kill a few minutes of time at the end of the workday while still appearing busy? Try the maddeningly frustrating yet addictive game called Red Square.
Red Square – mikemiller.net
As it game, it doesn’t get much simpler than this. All you do is click a red square once and hang on for dear life! That’s right, it’s a bit like bull riding.
Once you click the red square, the blue shapes will start moving automatically around the screen. The object of the game is to avoid conflict – if the red square runs into the wall or a blue shape, the game ends. Read more
