First Post in 6.5 Years
December 13, 2019 Reading time: 4 minutes
Hello, everyone.
Greeting and salutations! This is the first post for TipsFor.us in 6.5 years, and it's my personal first post in 7.5 years. Times have changed, that's for certain. What makes me create this post? I can't say for sure. While the site has effectively been dead for several years, I can't seem to let go of it. Perhaps I'm more tenacious than others.
Much has changed
Since 2013, the time of the last posting, the world is a radically different place, for the website as well as for its authors. From what I can tell, Everett is working full time as a programmer/developer. James is working a career as a lighting designer, and I (Brian), have been expending my efforts as a Professor of Music Theory and Composition.
As far as I know, Everett in living in Los Angeles, CA. James - to my knowledge - is living in Lawrence, KS, and I am living in San Antonio, TX. I can't speak for James, but I know that Everett has had two children, and I have had three children since our last significant posting. That's what ultimately led to the demise of the site: who had time to maintain a hobby website, once full-time careers and children came into the picture? Read more
Top 5 Script Kiddie Mistakes
July 10, 2013 Reading time: 5 minutes
These are the most common and most annoying mistakes I see in web development code on a daily basis. Well, Ok, it’s the things that annoyed me most TODAY, but it’s not unique. It’s mostly PHP and MySQL stuff here, but the same abuses take place anywhere the language allows it.
1. Database prefixes. I find so many database tables that use a “table” or a “tbl” prefix. Are you serious? Do you think we don’t already know it’s a table we’re looking at? Likewise, some developers find it somehow necessary to use “column” or “col” in their column names. I mean really… do you pin your own name upside down on your shirt? Seriously, this type of labeling is completely unnecessary and it probably reveals you as the half-baked amateur that you are. Label your column names descriptively: too little info is bad, but too much is no better.
The one exception I make to this rule is this: be verbose with your primary keys because you’ll use those in all of your join statements. I know it’s easier to code if every table uses the ubiquitous “id” as the primary key, but if you ever have to do complex MySQL joins for reporting queries you’ll appreciate the fact that user_id or post_id references the same thing no matter which table it’s used in. Read more
Help! My Site Was Hacked!
January 14, 2013 Reading time: 7 minutes
This can happen to the best of us. Hacks suck. There is no formulaic response to them that is guaranteed to fix your site, but I’m going to outline a few steps that might get you back in the saddle and hopefully help you identify the extent of the damage. The most common type of hack I see is against sites running known systems (like WordPress) where the hacker modifies the index.php file and prints extra code into the pages. This causes visitors to inadvertently download malicious code and it causes Google to black-list your site. Did this happen to you? Keep reading…
1. Verify that no sensitive data was on the server. It’s a whole other ballgame if you were storing credit card or social security numbers. In a nutshell, never store sensitive data on your server! It’s too hot to handle! Let a professional store that stuff. If you did have sensitive data on your server, you can stop reading now, because you need to hire a professional security consultant (and possibly a lawyer) to help dig you out of this mess. Read more
Securing Your Email via 2-Step Verification
January 11, 2013 Reading time: 3 minutes
It is vitally important to keep your email account as secure as possible. Google is one organization that emphasizes security, so take advantage of it! For Google Mail, it is easy to enable 2-step authentication. The idea is simple: in order to log in, you must provide something that you know (your password) and something that you have (your phone).
Think about this for a moment… normally if someone gets ahold of your email password, they could read your email (or impersonate you!). Think about it a bit more: once a hacker is in your email, they can visit other sites (like Facebook, PayPal, or ???) and they can easily click the “I Forgot my Password” link, and POOF: they’ll be able to log into any site that uses that email address.
The bottom line is that a hacked email account can start a chain reaction that can destroy your digital life. But with Google Mail, there are steps you can take to prevent this. Read more
How to Simply Rip DVDs in 64-bit Windows
July 8, 2012 Reading time: 4 minutes
![]() In the past, we’ve looked at how to easily rip DVDs on the Windows platform. That method still works great, unless you’re on a 64-bit version of Windows. For those of us now running Windows 7 64-bit, we have a problem: DVD43 – a required decrypter used in the previous tutorial, does not get along well with 64-bit versions of Windows.
In the past, we’ve looked at how to easily rip DVDs on the Windows platform. That method still works great, unless you’re on a 64-bit version of Windows. For those of us now running Windows 7 64-bit, we have a problem: DVD43 – a required decrypter used in the previous tutorial, does not get along well with 64-bit versions of Windows.
The Solution – Handbrake with libdvdcss
There’s an easy solution to this problem, and it only requires the installation of one software program. I’ve migrated to the mighty Handbrake for all my DVD rips. First, install the 64-bit version of Handbrake. As of this writing, the latest version is 0.9.6. Read more
Microsoft takes another hit: NGINX tops IIS
January 10, 2012 Reading time: 4 minutes
Some bloggers have suggested that ripping on Microsoft is going out of style… but this week Microsoft’s beleaguered IIS web server got bested by the open source NGINX web server.
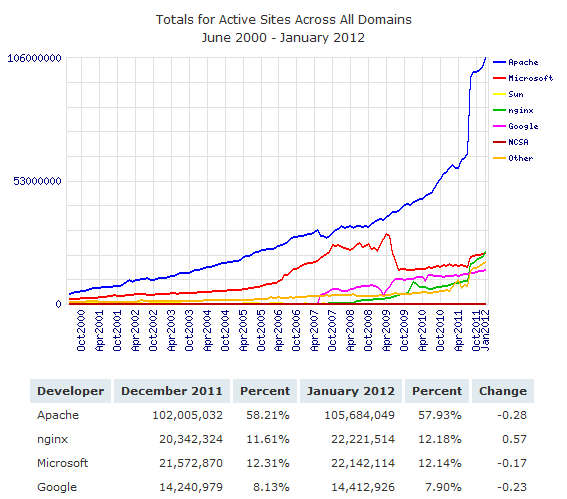
My beefs with Microsoft are many, however, I will tip my hat to Bill Gate’s many generous donations to charity. That’s really the most remarkable thing about Microsoft: it gave birth to one of the most magnanimous philanthropists of an entire generation, and no words can express thanks for that. Read more